IPv6 Covert Channels
Disclaimer
This post is ongoing
Originally IPv6 Covert Channels were the topic of my Master Thesis in CyberSecurity, In the last year I wanted to expand the topic and provide the community with a tool capable of instantiate such exploits easily in a network to test visibility and implement detections.
I have presented my work at Elbsides 2025, and you can find the slides available here
The code is available on GitLab. The published code does not include yet all the Covert Channels described in this article as an improved implementation is on-going.
Introduction
Inspired by the work of Luca Caviglione et al. "IPv6CC: IPv6 covert channels for testing networks against stegomalware and data exfiltration" I have implemented a Python based tool that allows the instantiation of IPv6 Covert Channels between to networked hosts.
The goal of the tool is to:
- Provide a reliable, repetable and easy way to instantiate IPv6 Covert Channels
- Implement data exfiltration capabilities between two hosts over a covert channel
- Be extensible and controllable.
Why IPv6 Covert Channels?
Since 2012, the adoption of IPv6 has seen an exponential growth rate, with an average annual increase of around 40%. This acceleration is largely attributed to several factors:
-
The increasing demand for IP addresses, driven by the proliferation of IoT devices and mobile networks;
-
The growing adoption of cloud computing, which often relies on IPv6 as a default protocol; and
-
The strategic efforts of major ISPs and tech companies, such as Google, Microsoft, and Amazon, who have been actively promoting IPv6 adoption.
For instance, in 2020, it was reported that over 30% of global internet traffic was already routed through IPv6 networks. As a result, the availability and accessibility of IPv6 addresses have improved significantly.
Another reason why I focused my attention on IPv6 Covert Channels is the rising adoption of hybrid cloud setups in enterprises could represent an additional communication link that relays on IPv6 based communication.
What is a Covert Channel
A simple definition of covert channels is the following:
"A covert channel can be defined as any communication channel that can be exploited by a process to transfer information in a manner that violates the security policy of the system."
Covert Channels in network protocols in a certain way can be compared to steganography techniques, in fact both use a carrier to send covert messages. The difference lies in the nature of the carrier itself, classical techniques in which the covert data hides in images, video, text or sound relies on a carrier of unstructured nature; while network covert channels' carrier is a network protocol, which, by nature, its a structured carrier. Allowing the transfer of information even when specific Firewalls rules are in place.
In more details IPv6 Covert Channels work by embedding data within the IPv6 Header or IPv6 Extension Headers acting as a carrier; altering reserved or unused fields.
Adversarial model
From an attacker perspective Covert Channels are suitable during the Command and Control and Actions on Objective phases of the Attack Killchain. Once a the attacker has gained access to a node, Covert Channels could be use to instantiate any remote command to the victim machine or for exfiltrating data without being noticed by Intrusion Detection Systems; such capabilities are instrumental in APT campaign where the secrecy of the covert communication is fundamental to implement multi-stage payload malware, coordination of botnets and sandbox bypass.
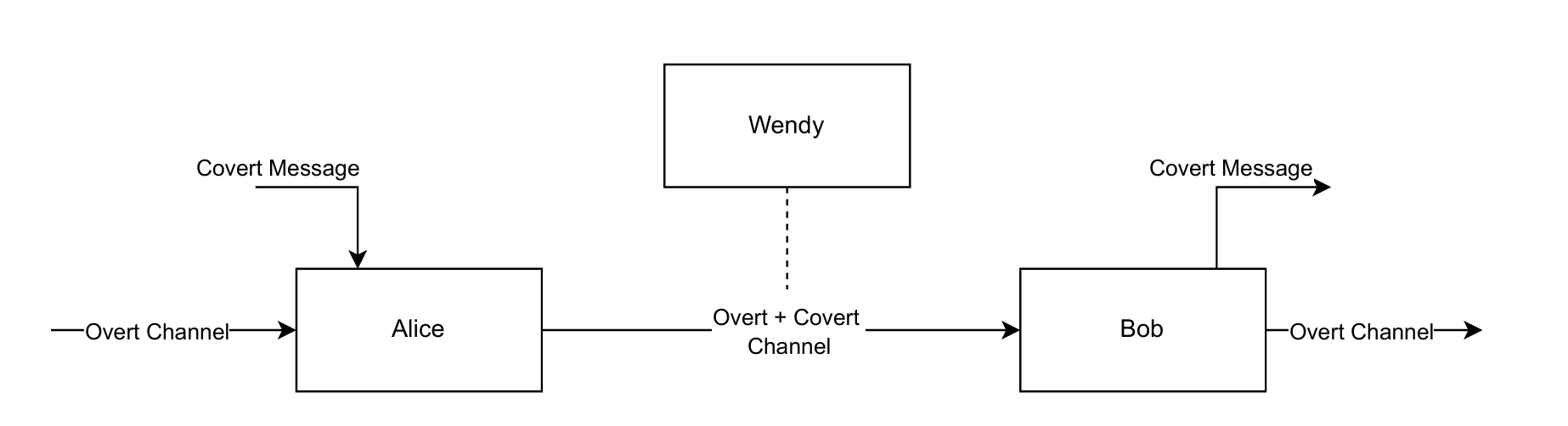
More formally we could also model the usage of a covert channel by using the Prisoners' Problem. Assume that Alice and Bob are two prisoners allowed to communicate only if Wendy, the warden, is able to check all the messages they exchange. The messages should look innocuous even if they contain useful information for planning their escape.
Covert Channels implemented
The tool is implemented in Python and the covert channels are implemented via a combination of iptables commands, Netfilter Queue and Scapy. At high level the tool works as follows:
- Writes an iptables rule that forwards all packets from a given source to a given destination in a Netfilter Queue.
- Bind the Netfilter Queue to a Python process that dequeue packets and,
- Depending on the role of the process (sender or receiver) data is inject or exfiltrated from the packet using Scapy.
and it implements covert channels that exploits the following components of the IPv6 Protocol:
- Flow Label - available
- Traffic Class - available
- Authentication Header - available
- Destination Options Header
- Routing Header
- Fragmentation Header
Implementation
Before diving into the implemetation of the single modules the roles that a machine can assume when running IPv6CC.
Roles
Sender. The sender is responsible of initiating the covert channel and of the data exfiltration. The sender set up involves: the creation of a specific Firewall rule, the splitting of the exfiltated data into chunks and finally the interception and injection of data into specific IPv6 packets destined for the receiver.
Receiver. The receiver is a node part of the hops of the communication between the sender and the legitimate end of the communication, or is both the recipient of the legit and covert communication. These two cases are differentiated by the flag: forward. If the flag is enabled the former case is selected.
Communication strategies
If one side of the coin is represented by the pure implementation of the covert channel, defined as the set of steps necessary to modify the IPv6 packets in order to hide the covert communication; the other side is represented by the implementation of communication strategies that would make the covert channel effective.
A simple communication strategy relies on the synchronicity between the sender and the receiver. Such naive approach requires that the receiver is instantiated before the sender starts sending covert data; such mechanism is not reliable for real-world scenarios as it depends on the transmission timing and it is not robust against packet loss.
For this reason, a more robust communication strategy is implemented. It consists on marking the stegopackets with a specific secret constructed by the sender starting from a common secret and a hash function which is verified by the receiver.
Modules
The first component of the IPv6cc library is the FirewallHandler module, responsible of setting up the necessary firewall rules. The module is implemented as a façade that provides a simple interface to the user allowing to implement additional firewall support if needed. FirewallHandler is the fundamental building block for the covert channels as it allows the interception of packets.
The second building block is the FileChunker module; which is responsible of the data handling of the covert channel implementation. The idea is to provide a realiable way to split data into chunks of a fixed size that can be easily adjusted depending on the specific requirements of the covert channel used; the module provides also the inverse operation allowing to merge chunks into a single file. In addition to these simple operations the module provides also the ability to create hashes of data chunks and verify their integrity. The integrity check is part of the covert channel process as it allows to detect errors in the data transmission.
The last module is CovertChannel module, responsible of the implementation of the different covert channels by providing a simple interface that allows users to easily implement additional covert channels.
The covert channels fully implemented in this new version are:
- AuthenticationHeader
- FlowLabel
While the traffic class is implemented not as stand-alone covert channel but as part of the FlowLabel covert channel in reliable mode.
Covert Channels
Even if each covert channel has its own specific implementation, they all share a common structure and interface that it is respected to ensure ease of maintainability, expansion. Such interface is responsible also for the implementation of all common operations that are required, such as data splitting, merging and integrity checks.
Authentication Header
The implementation of the Authentication Header covert channels starts with analyzing the specification document RFC4302.