Case Study: Panoptesec System
Table of Contents
1. Last Lecture
- Class: Security Governance
- Topic: Risk Analysis
Panoptesec is the result of an European project:
It has the goal to provide support to the security operator during risk estimation, finding mitigation actions, and provide support during the reactive phase, so when the system is under a potential attack, predicting the possible next action of the attacker.
2. MAPE-K
The paradigm used is well known in the control engineering field, it is the implementation of a feedback loop, that starts from the monitoring of the infrastructure, then data collected is analyzed and then the analysis is viewed over a model that represent an high level of the system executing in an automatic, or semi-automatic actions.
At the center of the loop there exist a knowledge base used to improve the analysis and planning section.
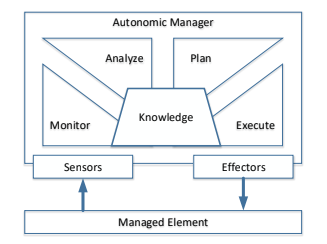
2.1. Architecture
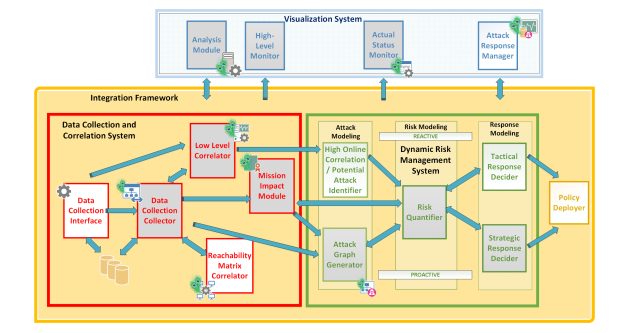
There are two different kinds of analysis achieved by the system: proactive analysis or reactive analysis. In the second part, online data is used, and is used to infer if there is a potential attacker on the system, and tries to predict where the attack will go suggesting immediate countermeasure.
The yellow box is called policy deployer, it is a component that can potentially execute some mitigation actions automatically (block some ports on the firewall, send notifications, actuate actuators). Practically speaking it was implemented only as notification component, but conceptually it can perform automatic actions.
The Visual analytic system is the front-end showed to the user, so it is the interface provided by the system. Internally there’s a lot of application logic that displays data in the most useful data and automatically adjust to maximize the support to the operator.
On the attack graph there is the view of the system at a technical level, so it is possible to explore the ways that the attacker can use to move inside the system. The entry point is easy to identify, but the target depends on the business. The target is inferred by the system because it represent the necessary conditions needed to provide the service provided by the machine (business impact model). The system provides a representation of the dependencies between the services provided and the machines that supports the business.
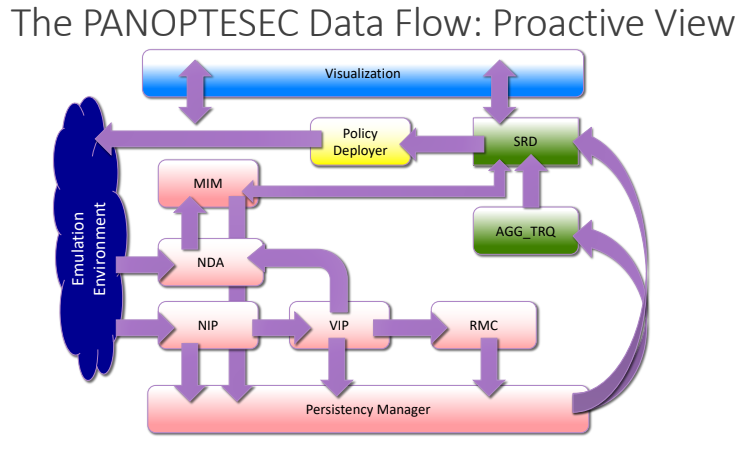
- Pink components are the… MIM component was responsible to infer the dependencies between the… NIP receives the information from tools like nmap, and translates them into a predefined JSON, VIP is the vulnerability inventory: it takes the output of vulnerability scanners, and merge the data, RMC computes the reachability matrices, the persistency manager stores data needed for the attack graph generation.
- Green components are … AGGTRQ generates the attack graph, and compute likelihood of different paths, SRD computes mitigation
- Yellow
2.2. Threat risk quantifier
Starting from elementary risks, then analyze the attack path, and link the target of the attack path to the business element, inferring the impact that the compromission of a CIA property on the host will have on the business process.
The system is able also to estimate the possible damages in term of money.
The second step is to map every attack scenario with its on level, and estimate the impact, then they are aggregated and a table is created as input for the planning phase.
The idea is that an attack path is the sequence of consecutive exploits, the exploit has a certain probability of success, and it takes a certain time to be executed. This means that when on a given node of the path its possible to compute a probability that indicate if the attacker will move to another node in a given time.
The path can be computed as a Markov Chain, that allows to estimate the probability to reach the last node of the chain.
The likelihood is smaller if the length of the path is longer (decibel scale).
\(\lambda_k\) is computed via values obtained from the CVSS. It is the exit rate needed to model the Markov Chain.
Moving to version two and version three of CVSS some values are changed, but more or less it is possible to map the two scoring versions, keeping in mind to be consistent to the